🎉 GitGuardian raises $50M Series C to accelerate AI agent security and NHI governance 🤖
3
🎉 GitGuardian raises $50M Series C to accelerate AI agent security and NHI governance 🤖
3


Public Secrets Monitoring
GitGuardian monitors GitHub round the clock for your secrets and sensitive data. We catch the leaks, you stop the intrusions.
.svg)
90+ Million developers | 300+ Million repositories
Even if your company doesn't do open source, chances are your developers do. And they may be unintentionally leaking your corporate secrets or source code on their personal GitHub repos - without your knowledge.


















GitGuardian has absolutely supported our shift-left strategy. We want all of our security tools to be at the source code level and preferably running immediately upon commit. GitGuardian supports that. We get a lot of information on every secret that gets committed, so we know the full history of a secret.
Find out how GitGuardian keeps your organization safe from GitHub threats
Organization repositories monitoring
Monitor the official public repositories listed under your GitHub organization.
Developers’ personal repositories monitoring
Monitor developers’ personal public repositories – this is where 80% of corporate credentials are leaked on public GitHub. GitGuardian identifies under-the-radar activity by automatically linking developers, public commits, and repositories you may be unaware of to your organization’s dynamic perimeter.
Exposing dangerous blind spots
Identify secrets within commits supposedly deleted, but still visible within GitHub network of forks.
Specific detectors
GitGuardian's specific detectors support 350+ API providers, database connection strings, SMTP credentials, certificates...
Generic detectors
Capture JWT secrets. Bearer tokens, username/password pairs, and all types of high-entropy patterns not covered by specific detectors with GitGuardian's "Paranoïd mode".
High precision detection
Reduce alert fatigue with a 91% True Positive Rate (TPR) and the grouping of multiple instances of the same incident in one alert.
GitGuardian performs contextual analysis of the surrounding code to discard false positives and weak matches. When possible, GitGuardian also checks the validity of the detected secrets with non-intrusive HTTP calls to the host.
Keyword match
Track keywords on public GitHub to look for your organization’s internal project names, reserved IP addresses range, domain names, or any other type of sensitive data.
Explore – GitHub search
Use Explore, GitGuardian’s search engine to scour more than 12 billion documents on public GitHub for sensitive data. Save your queries in your library and schedule periodic runs.
Real-time alerting
GitGuardian’s Mean-Time-To-Detect is a few seconds after the secret is publicly exposed.
Developer alerting
Developers are at the forefront of the issue of secrets leaks. GitGuardian alerts the developers involved in the incidents alongside your Security team.
Integrations
Connect GitGuardian to your SIEM, ITSM, ticketing systems, messaging apps or configure your own webhooks.







Incident severity assignment
Start from templates and create custom rules to automate incident severity assignment.
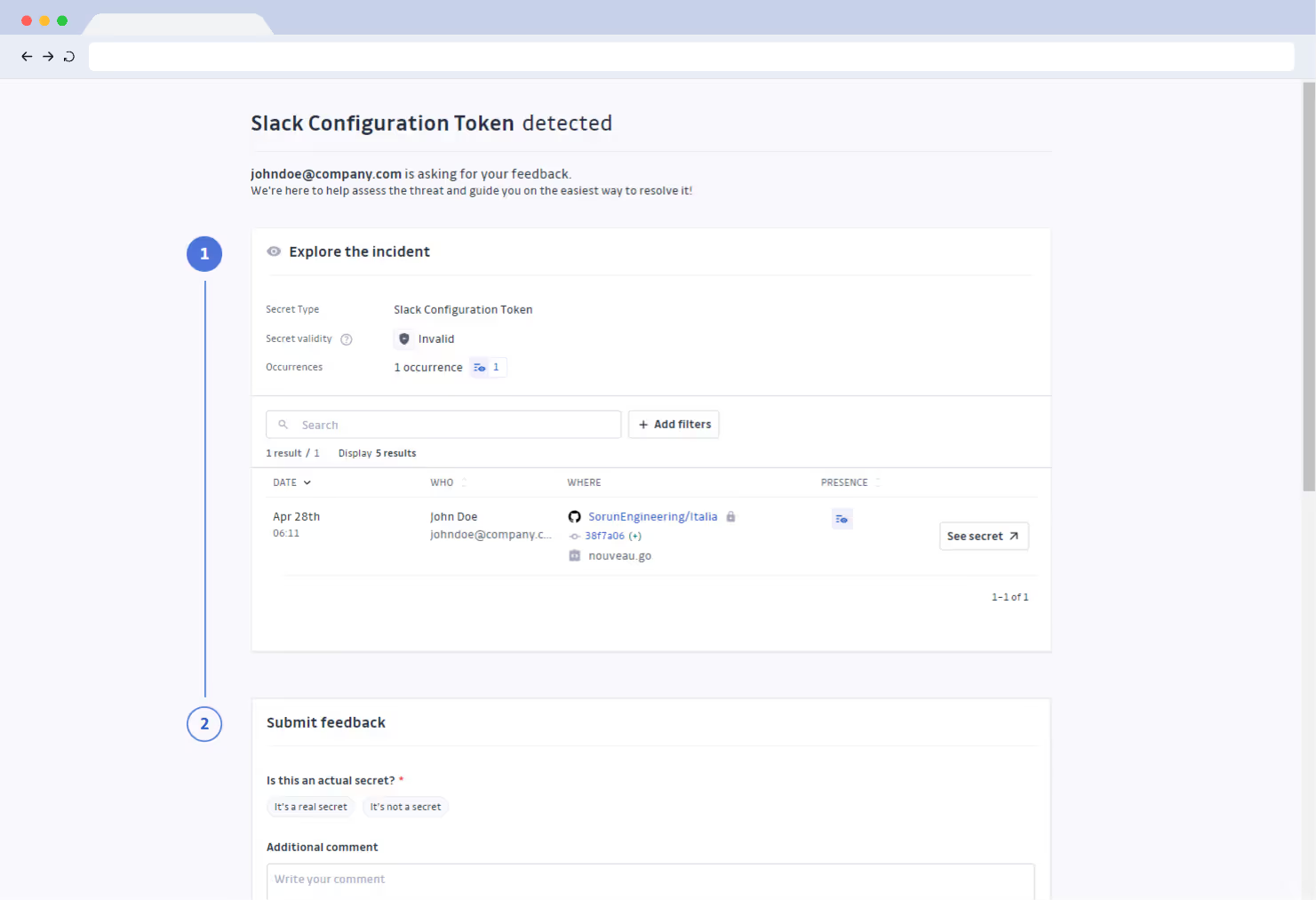
Incident prioritization
Explore and triage your incidents with key context information: secret type, location (repository and files), incident severity, number of occurrences, live presence on GitHub, secret validity.
Developer feedback collection
Generate unique links to collect developer feedback on incidents. Harness the involved developers’ knowledge to understand the nature of the incident and its potential impact on your company or client systems.
Programmatic incident handling
Manage incidents programmatically with a REST API.
SSO
Single Sign-On functionality, compatible with any SAML 2.0 provider.
Audit logs
Browse detailed activity logs of all actions triggered on the dashboard or through GitGuardian’s REST API.
Roles and permissions
Control user permissions in the GitGuardian dashboard with "Admin" and "Member" roles.
And keep your secrets out of sight